Latest reviews
In Arrival of the Fittest (review), biologist Andreas Wagner made the compelling argument that life “finds its way” to solutions by way of neutral mutations. Through incremental changes, proteins can change shape gradually without losing their original function. As a population diversifies, natural selection can then identify those protein variants that have acquired entirely new, useful functions.
The book challenged a naive view of evolution, in which the vast majority of genetic mutations cause harm, and a small percentage of them confer an immediate survival benefit. The truth is that life needs to “play around” with neutral mutations to navigate the landscape of possible changes that may make a species more or less suited for survival.
In Life Finds a Way, Wagner applies this “landscape thinking” to all types of creative problem-solving. The first half of the book focuses on the concept of fitness landscapes, a limited but useful visual metaphor for how well-adapted specific genes (and the creatures they inhabit) are to their environment. The peaks in a three-dimensional landscape represent high levels of successful adaptation to the environment:
Visualization of a population of individuals evolving to become better suited for survival, i.e. “climbing a peak” in the fitness landscape. (Credit: Randy Olson and Bjørn Østman. License: CC-BY-SA.)
Natural selection marches steadily uphill. What prevents a population from being trapped on a small hill that represents an evolutionary dead end, an adaptation of limited usefulness that can’t be improved? Wagner breaks down how genetic drift (changes in frequency of specific gene variants), genetic recombination through sexual reproduction, and horizontal gene transfer in bacteria help individuals in a population slide or jump across the fitness landscape.
Wagner shows how potential energy landscapes in physics can similarly be used to map the possible configurations of molecules or crystals, and how gravity, thermodynamics and other physical forces push nonliving matter into stable (and often beautiful) configurations that represent valleys in the landscape.
Of mountains and molehills
In the second half of the book, Wagner applies landscape thinking to human creativity. He encourages us to visualize the map of creative solutions to a given problem (even if that “problem” is the composition of beautiful music) as a landscape with peaks and valleys. What does it take for a creative mind to climb mountains and avoid getting stuck on molehills of mediocrity?
The author enumerates many tools creative minds can use to traverse the landscape of ideas without getting stuck, including:
-
dreams
-
play
-
travel and exposure to other cultures
-
work with people from other disciplines
-
drugs.
As a positive model for cross-disciplinary work, Wagner cites the Santa Fe Institute, a renowned cross-disciplinary think tank where Wagner is an External Professor. (One way I hope they won’t be a model: even though the institute was only founded in 1984, its seven founders were all men, something Wagner does not remark upon.)
Into the badlands
Wagner harshly criticizes the obsession with standardized testing in the United States, and the rigid education approaches of South Korea and China. In his critique, he revisits familiar generalizations about “Western” and “Eastern” cultures, and seems to see “Eastern” cultures trapped in rigid uniformity, while situating the pinnacle of individual freedom in the United States.
Nations that want to nurture creative minds, Wagner argues, should reduce the negative consequences of failure—whether it’s for scientists applying for a research grant, or for entrepreneurs starting a business. Creative societies should be accessible to immigrants with diverse backgrounds, and recognize the benefits of diversity and individual freedom.
While Wagner pays lip service to the dangers of inequality, his analysis is stuck in a neoliberal frame of reference. Much more could be written about how an effective welfare state, a vibrant democracy, and alternatives to exploitative capitalism and intellectual monopoly rights (copyright, patents, etc.) are necessary to reap the benefits of human creativity for all people.
Instead, Wagner repeatedly cites Silicon Valley as an example for innovation, with the implicit assumption that the way to make a better world is to create more corporations like Facebook, Apple, and Tesla.
It’s worth remarking that Life Finds a Way was written before the COVID-19 crisis laid bare the utter incompetence of many “Western” governments, including the United States, in managing a pandemic. The landscape of ideas about COVID-19 is dotted with the creative edifices built by anti-vaxxers and ideologues, and landscape thinking alone seems like a very limited tool for getting humanity out of the badlands.
Thankfully, Wagner’s flurry of societal prescriptions is as brief as it is unimaginative. What we’re left with, then, is his argument to apply landscape thinking beyond physics and biology, providing an intellectual foundation for the value of letting our minds roam. That’s all it is—a foundation, one which I do hope other writers will build on.
Das Vegs ist die einzige komplett vegane Gastronomie in Halle. Es gibt ein breites Angebot an Wraps, Burgern, Fladenbroten und weiteren Speisen.
Es gibt innen ein paar Plätze und bei schönem Wetter kann man sich draußen hinsetzen. Die Atmosphäre entspricht einem Fast-Food-Bistro.
Da es mir gut schmeckt, bin ich regelmäßig dort.
Damn the Vek! Too stupid to communicate with, but smart enough to seek out human civilization wherever it is. In every timeline, the plague of giant insect monsters is close to wiping out what’s left of humanity. They breed underground and tunnel their way to the surface, only to bring death and devastation.
Insecticide won’t kill these bugs dead, but a squad of piloted battle mechs might. Or might not. Fortunately for the multiverse, humanity has learned how to travel between parallel universes, to attempt to rescue as many timelines as possible from the Vek.
Once more Into the Breach then, with another squad! Released in 2018, the second title by Subset Games after FTL cemented the tiny indie studio’s reputation for excellence. It takes plenty of inspiration from legendary turn-based strategy games (Advance Wars especially comes to mind), but still feels fresh and unique.
Much of this is due to the tightness of gameplay and mechanics. Assemble your team. Click. Pick a scenario. Click click. And: you’re in the fight. The map fits on one screen. You place your units. The enemy moves. The enemy starts to attack—and now it’s your turn.

A member of the Zenith Guard, a charge mech, finds its target. (Credit: Subset Games. Fair use.)
Depending on your squad and each mech’s buildout, you can destroy units, push and pull them, create hazards, create shields, and more. The array of skills turns every round into a small puzzle. How will you prevent the enemy from damaging your units, or killing civilians in a building, or destroying strategic targets?
Miscalculate, and the Vek might end up taking down the energy grid—game over. It’s permadeath, sort of: you can take one of your pilots to the next timeline. Too bad for this one.
An Honest Roguelike
From a limited number of ingredients, the game cooks up a fresh set of scenarios for you on each run. Some maps are especially difficult to beat without taking some hits to buildings; any damage you take to the energy grid carries over to the next map. You have to make some strategic choices between battles—which battles to fight, which upgrades to install—but most of the game is tactics, tactics, tactics.
The difficulty level is not quite as punishing as that of FTL or other roguelikes that celebrate starting over as part of the fun. At normal difficulty, you may notch your first game victory after a few runs, perhaps even on the first try. The Vek are as stupid as they are relentless. But the game will produce enough brain twisters to keep you coming back.
When you manage to shove a nasty Vek into the sea, or cause a chain reaction of monsters killing each other, it’s quite the payoff. If that isn’t enough, the game rewards you with unlockable squads, experience points, upgrades, and ambient dialogue that never gets in the way.
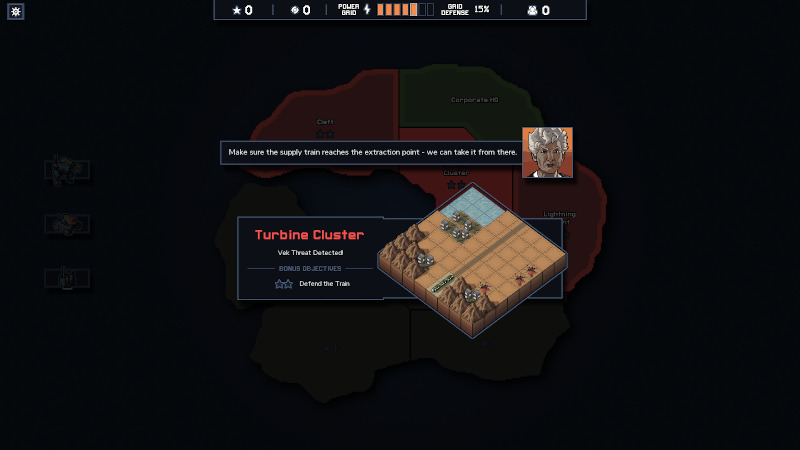
Mission briefings are terse, but there’s a large enough variety of objectives to keep things interesting. (Credit: Subset Games. Fair use.)
The Verdict
While it’s a very different game than FTL, it’s clearly built with the same design philosophy. The pixel art is more beautiful than FTL’s, but never extravagant; the UI provides help when it needs to and otherwise gets out of the way; moving your units feels as straightforward as moving the pieces on a chessboard.
In spite of the absurd premise and cartoonish physics (units can be encased in ice and unfrozen without damage), the game’s tone is mostly somber; even victory is just a brief reprieve in an endless war played out across universes. The fun is in solving the puzzles the random number generator throws at you and kicking some serious Vek butt. If that kind of turn-based strategy sounds like your cup of tea, you can’t go wrong heading Into the Breach.
Klein aber fein ist dieses Hotel im Zentrum Heidelbergs. Vom Hauptbahnhof sowohl zu Fuß als auch mit öffentlichen Verkehrsmitteln sehr gut zu erreichen und daher auch eine ideale Ausgangslage für Aktivitäten in der Stadt.

Aussenansicht des Hotels Tannhäuser in Heidelberg (Eigenes Werk. Lizenz: CC-BY-SA.)
Das es kein durchdesigntes Hotel einer ausstauschbaten Kette ist merkt man schon beim Betreten des Hauses und auch die Zimmer machen einen sehr guten Eindruck. Wenn das Standardzimmmer hier schon größer ist als anderswo eine Suite dann freue ich mich darüber.

Ansicht eines Zimmers im Hotel Tannhäuser in Heidelberg (Eigenes Werk. Lizenz: CC-BY-SA.)

Ansicht eines Zimmers im Hotel Tannhäuser in Heidelberg (Eigenes Werk. Lizenz: CC-BY-SA.)
Das Frühstücksbüffet bietet alles, wirklich alles, was ich in dieser Kategorie erwarte. Keine abgepackten Marmeladen, Discountersalami oder Aufbackbrötchen. Alles ist frisch und - auch noch um 9:30 Uhr - reichlich vorhanden. Im Hintergrund läuft leise Musik und man kann gemütlich und satt in den Tag starten.

Frühstücksbuffet im Hotel Tannhäuser in Heidelberg (Eigenes Werk. Lizenz: CC-BY-SA.)
Einziger Wermutstropfen ist der bereits oben erwähnte Nahverkehr. Die Straßenbahn hat direkt vor dem Hotel mehrere Kurven und Weichen zu passieren. Mit Ohrenstöpseln aber kein Problem.
Cursed Sight is a visual novel developed by Marcus “InvertMouse” Lam, an Australia-based indie developer. We meet the protagonist, Gai, at the age of 10 when he is sold by his parents to work as a servant for the king of East Taria, a fictional Asian kingdom. Gai becomes responsible for helping to protect the kingdom’s “treasure”—a young girl named Miyon born with dangerous abilities that King Lok is exploiting.
As the story progresses, Gai develops a friendship with Miyon and her caretaker, a young woman named Sasa. As Gai and Miyon grow older, they consider what kind of life may be possible beyond the captivity of the temple. Their decisions could cost them their lives, and they will certainly shape the future of the kingdom.
This is a mostly kinetic visual novel, meaning that you read it by clicking through it. There are 4 different endings, which you access through a couple of branch-points in the story where you do get to make choices.

Miyon is a young girl who is held captive to exploit the mysterious power of her cursed sight. Beautiful screens like this one are used as segways between different chapters of the story. (Credit: InvertMouse. Fair use.)
The art is lovely, and the music, while repetitive, fits the setting. The story is not voiced. The writing is decidedly mixed. Gai never quite acts his age (his 10-year-old version is too adult, his adult version is too childish); some paragraphs really needed an editor; anachronistic references and expressions distract from the setting. The most cringeworthy example is this one:
Miyon had opened up so much that I worried the other servants, or even guards, might become interested in her. I would fight them all in a cage at the same time if they dared touch her. Well, maybe after I attached a chainsaw to my left arm.
(Yes, that’s a reference to a chainsaw in a game that is meant to be set in the distant past.)
The game is at its strongest when it conveys emotions and builds its characters. I certainly became invested enough to finish the story and to get to all four endings, and the story moved me to tears a couple of times. While the game is only of average quality overall, there’s the kernel of something lovely here, and I look forward to playing more of InvertMouse’s games in the future.
Bad writing grasps at your attention like a man grasping at straws; great writing seizes your attention and doesn’t let go. Eliza is a computer game, and its writing is firmly in the latter category; it has a story to tell, and the moment it begins telling it, you want to know how it ends.
This is a visual novel, a genre in which you typically click your way through an illustrated story and make a few choices along the way. You play as a young woman named Evelyn who, after a period of depression and burnout, starts a job working for an AI-based counseling service called Eliza (in homage to the 1966 chatbot of the same name).
Evelyn works as a proxy, a human face for the AI. Proxies are required to faithfully read their lines to customers—”don’t deviate from the script!” Some of the people Evelyn meets as a proxy are looking for treatment, some just want a person (or a machine, as the case may be) to talk to. The game uses this conceit to explore deeper questions about the role of technology in a capitalist society.
As an undercurrent, Eliza explores the culture of the tech industry. There’s the startup founder with the grand vision of “ending human suffering”, who seems to harass every female staff member he hires. There’s the idealistic young engineering manager who is starting to raise questions about the privacy practices of his employer. And there’s Evelyn’s friend Nora, a former programmer who is now freelancing and making electronic music.

Evelyn (right) meets her colleague Rae for a cookie-baking session. (Credit: Zachtronics. Fair use.)
The game offers small choices throughout, but their effect tends to be very limited. In fact, when you act as the AI’s proxy during counseling sessions, the game deliberately takes away your choice to say anything other than the dialogue generated by the AI, occasionally forcing you to say “I’m sorry, I don’t understand the question” as if you yourself were an algorithmically constrained chatbot. It’s player frustration in service of the story.
At the end of the game, Evelyn must make a defining choice, which leads to one of several endings. The game does not punish or reward you for your choice with a “good” or “bad” ending; instead it concludes the story in a manner that suits the character you’ve chosen to become.
Eliza took me about 6 hours to complete, and that includes exploring the different endings. The dialogue is fully voiced by a cast of experienced voice actors. Backgrounds and character sprites are visually pleasing, but the graphics are completely static—facial expressions or poses don’t change, even when the dialogue suggests that they should.
The Verdict
Eliza falls a bit short on the “visual” side of being a visual novel due to its use of static images; as a game, some players will find its linearity and long sequences without significant player choices overly limiting. But as a story about the role of AI in society, it is gripping and timely. If the theme interests you, I recommend the game without reservations.
Every once in a while, I’m drawn to the tower defense genre, where you must dispatch with waves of enemies by building stationary defenses that fire on anything that moves in their proximity. It’s real-time-strategy reduced to the barest explodey foundations, with all action often taking place on a single screen. Unsurprisingly, the genre thrives on tablets and other mobile devices.
Cursed Treasure 2 differs from the stock formula mainly in two ways: You play as an evil overlord, and your enemies are trying to steal your stuff (gems in this case). If they steal all of it, you lose the level. That gives the player a more active role in the proceedings—you have to always keep one eye on those gemstones to prevent your enemies from absconding with them. If you have enough mana, you can summon a meteor to smush your opponents, or you can strike terror into their hearts to deter them.
After winning a level, you can play it in “night mode”, which restricts your placement options for towers to add a bit of difficulty; between levels, you can spend experience on assorted power-ups. All in all, the game offers enough variety to keep things interesting for a while—I put about a dozen hours into it.

Fighting one of the bosses in the last level. (Credit: Armor Games Studios / IriySoft. Fair use.)
The downsides:
-
There’s no story to speak of, and some of the English text on the screen would have benefited from copyediting by a native-level English speaker.
-
The game crashed once on me, and it forget its savegames a couple of times (restarting the game again made them re-appear).
-
By the time you’re really comfortable with all the mechanics, the game is over; unless you’re a dedicated completionist, night mode just doesn’t offer enough to pull you back in.
Still, you can often pick this up for a dollar, and it’s a solid game with a decent Linux port. Recommended if you’re like me and occasionally just want to fill your screen with things that go boom.
One of the main reasons for why $DOT has been receiving so much attention lately in the cryptocurrnecy space (particularly in the markets) is because of the project’s promise of future interoperability with Ethereum, Bitcoin, and a plethora of additional cryptocurrency protocols.
Below is a graphic from the project’s documentation that illustrates what this connection / bridge would look like within the Polkadot ecosystem:

While this bridge is highly theoretical and contingent on the project’s ability to succeed at something that has effectively never been done before, it appears that the overall blockchain markets are highly optimistic that this plan will come together.
Breaking Down Polkadot’s Proposed Bridges
Documentation on these proposed bridges by Polkadot can be found on their ‘wiki’ here: https://wiki.polkadot.network/docs/en/learn-bridges#bitcoin-bridge
Evaluating the Plans for a Bitcoin Bridge
Since this is presented first in the documentation’s order, we figured it would be prudent to make this our first destination for closer scrutiny / analysis.
Usually we wouldn’t take too much time to look into a project’s technical merits in this manner, but since Polkadot’s success in this endeavor has massive implications for the future of the project (especially its price action).
The specification for the Bitcoin bridge is depicted below:

What is ‘XClaim’?
The hyperlinked word ‘xclaim’ takes us to a whitepaper titled, ‘XClaim: Trustless, Interoperable Cryptocurrency-Backed Assets’

The whitepaper itself is fairly short, so let’s take a look into what its saying.
Per the Abstract:
“XClaim offers protocols for issuing, transferring, swapping and redeeming CBAs securely in a non-interactive manner on existing blockchains. We instantiate XClaimm between Bitcoin and Ethereum and evaluate our implementation; it costs less than USD 0.50 to issue an arbitrary amount of Bitcoi-backed tokens on Ethereum. We show XClaim is not only faster, but also significantly cheaper than atomic cross-chain swaps.”
From the Abstract, its relatively simple to tell that what is being proposed here is not something that’s based on a trustless protocol.
Reason Why This isn’t Trustless
Because Polkadot itself is not trustless. But it does provide a great framework for someone that would like to construct a trustless blockchain protocol.
The reason why is due to the consensus mechanism that Polkadot uses. Proof of Stake can never be considered ‘trustless’ by default because it requires a certain fault tolerance be met in order for the blockchain to continue.
If that fault tolerance is not reached, then the blockchain will halt entirely.
This was witnessed with Solana recently.
Solana Blockchain Halt Foreshadows Polkadot
In case readers are not aware, Solana’s entire blockchain came to a halt in the beginning of December due to what the developers of the protocol called a ‘bug’.

source: https://www.coindesk.com/solana-devs-call-all-hands-on-deck-as-unknown-bug-stops-block-production
Quick Side Note: Solana is also funded by the same venture capital firm that backs Polkadot, which is NGC (NEO Global Capital); notice how both projects have had excellent performances this month. Remember this and remain mindful of the fact that cryptocurrency markets are rarely, if ever, propelled by genuine technical advancements and very few development teams are motivated or capable enough to make said advancements that they propose. Thus, to their credit, they remain the world’s greatest fiction writers alive.
Before we get into Solana, its worth taking a second to step aside and prove the claim made above about NEO Global Capital’s (NGC) involvement in the protocol:

Notably, Multicoin published a report back in 2019 titled, ‘Binance is Blitzscaling’, in which they praised the exchange and also disclosed the fact that they were owners of the BNB tokens.
That statement can be seen below:

source: https://multicoin.capital/2019/11/07/binance-is-blitzscaling/
According to Multicoin, blitzscaling is defined in the following passage (just an fyi; a bit of insight into Binance’s inner workings):
“When you blitzscale, you deliberately make decisions and commit to them even though your confidence level is substantially lower than 100 percent. You accept the risk of making the wrong decision and willingly pay the cost of significant operating inefficiencies in exchange for the ability to move faster. These risks and costs are acceptable because the risk and cost of being too slow is even greater.”
One key part that many seem to have missed however, is the fact that Binance has made it openly known that they shift their user’s assets to other investments (illegally, of course, since they are not registered in any capacity to do so and certainly aren’t providing any transparent accounts of where those funds go + users are not given interest).
Specifically, Multicoin states:
“* Binance now automatically stakes their users’ assets on their behalf and distributes the yield back to them. This incentivizes users to keep assets custodied on Binance and unlocks the ability to quickly trade those assets without the need to unstake them and send to an exchange. This drives more liquidity on the Binance exchange and more assets custodied with Binance, which in turn drives greater network effects.*”
Hmm, not quite. By enticing users to “lock” their assets up with Binance in exchange for the ability to stake on their platform to yield returns in assets of questionable / no value, Binance is able to essentially able to pay people in fraudulent / fake money in exchange for the ability to use their funds to realize potential profits gained from them while they’re being “locked up”.
Since there is no way to validate that those funds are actually locked up, there’s no reason for why users should assume that they are. Instead, it is much more likely that said funds are being put to use for Binance to trade against users on the same exchange or engage in higher level ‘DeFi’ protocols within the space or slightly outside of it (i.e., with Genesis Trading or another entity of that nature).
BTC Parachain Documentation
According to the documentation:
“The BTC Parachain connects the Polkadot ecosystem with Bitcoin. It allows the creation of PolkaBTC, a fungible token that represents Bitcoin in the Polkadot ecosystem. PolkaBTC is backed by Bitcoin 1:1 and allows redeeming of the equivalent amount of Bitcoins by relying on a collateralized third-party.”
Then they provide the following graphic:

Everything in their description is fine up until the point that they claim that it, “Allows redeeming of the equivalent amount of Bitcoins by relying on a collateralized third-party”.
The main issue here is in the introduction of concepts that are not externally valid on the Bitcoin protocol (breaking the trustless property and thus, creating an unauditable pipeline / transferral of funds - something that is the antithesis of blockchain’s purpose).
Below is a diagram of how Polkadot intends on providing interoperability with Bitcoin:

As we can tell from the chart above, the Bitcoin that is being exchanged is supposed to somehow be “locked” and this ‘locking’ action will trigger the issuance of tokens called, ‘PolkaBTC’. Accordingly, Bitcoin has to be redeemed by “burning” PolkaBTC tokens.
Major Issue in This Scheme
As we move on, we can see that they validate that the transaction to the ‘XClaim protocol’ has occurred by mandating the turnover of the transaction ID as well as the block header of the block containing the relevant transaction.
The documentation even includes a graphic that shows the proposed workflow for this exchange (which results in the issuance of PolkaBTC):

Getting into the Major Issue
The major issue here is not in the design of the workflow. Its logically valid and there’s no reason to assume that it wouldn’t work.
But the issue comes in ensuring that the Bitcoin are not moved afterward.
For instance, if John decides to send 5 BTC into this ‘XClaim’ protocol, minting 5 new PolkaBTC for himself within Polkadot’s ecosystem, what is to stop John from then moving those 5 bitcoins back to his own wallet before redeeming those 5 PolkaBTC for 5 free bitcoins?
The documentation mentions a lot about “locking” bitcoins on the Bitcoin protocol, but there are are no specifics given as to how this process would take place in a manner that:
-
Ensures that the sender no longer has access to said bitcoins (or ensures that only they have access if they’re supposed to be redeeming these PolkaBTC directly for their Bitcoin)
-
Guarantees that the Bitcoin remains locked in a manner that is actually trustless and also valid on the Bitcoin protocol itself (if it is outside of the Bitcoin protocol or relies on schemes / structures foreign to the protocol, then we must consider the implementation to be completely ‘hypothetical’ in nature until the final payout is settled).
Seeking More Information
There is a chance that the documentation we read above simply does not contain the relevant details on how Bitcoin is supposed to be “locked” during this ‘swap’ (and why this would need to be collateralized if the swap is 1:1 with these minted PolkaBTC tokens).
Additionally, there was nothing included in the documentation that indicated that nodes on Polkadot would be running a Bitcoin client, so its not yet known how the protocol would be able to gauge whether the block header + transaction ID that they’re receiving is legitimate without also running a Bitcoin full node.
To find out more information we visited the official GitHub repo for the ‘BTC Parachain’, which can be found here: https://github.com/interlay/BTC-Parachain
It appears that we need to look more closely at the ‘collateral’ section in order to ascertain how this “locking” process is to take place:

Clicking the link above takes us to the part of the master tree that contains the code for the implementation of the ‘collateral’ module:

This may seem like a deadend, but it isn’t.
By examining the ‘cargo.toml’ file here (appears this is written in Rust, good choice), we find a link to the documentation included within the ‘notes’ of the code:

Bingo.
For those that wish to inspect this link for themselves, the one present in the code at the time of visit is: https://interlay.gitlab.io/polkabtc-spec/spec/collateral.html
Which should take users here:

Unfortunately, this specification contains little to no information on how the Bitcoin is to be locked.
Below are the excerpts from the documentation that mention anything about “locking” (which seems to mainly be in reference to the ‘collateral’ rather than the Bitcoin itself ; it is still unknown what the collateral is supposed to be, how it will be valued [oracles, likely], or why it is necessary):


Another problem can be found directly in the ‘overview’ section where it states:
“The Collateral module is the central storage for collateral provided by users and vaults of the system. It allows to (i) lock, (ii) release, and (iii) slash collateral of either users or vaults. It can only be accessed by other modules and not directly through external transactions.”
The fact that this collateral module can only be accessed by other modules and not via ‘external transactions’ means that we’ve abstracted beyond the Bitcoin blockchain - which makes it even more important for us to question how the bitcoins are being locked up or how we can prove a transaction unless the network is running Bitcoin full nodes.
Further Problems Caused
Unsurprisingly, the faulty foundation upon which the ‘interoperability’ protocol for Polkadot is based on leads to even greater calamities further along down the line.
We can see this clearly in the specification for the ‘PunishmentFee’.
Specifically, the documentation states:
“If a Vault misbehaves in either the redeem or replace protocol by failing to prove that it sent the correct amount of BTC to the correct address within the time limit, a vault is punished.”
Again, there are a couple of logistical issues here - and the first one is going to sound stupid, but its legitimate.
Major Issue With Time-Based Punishments: How is ‘time’ determined?
This may seem like a no-brainer, but we need to remember that we’re talking about blockchain, which means that these networks are p2p (peer-to-peer).
Thus, if this network is decentalized (and Polkadot furiously states that they are), then messages must be propagated to the network.
In other words, there is no way for one node to inform the entire network of an event all at once.
The node must spread the information to a certain subset of nodes that it is connected to, then those nodes must spread that information to other nodes and so forth until that information is propagated across the protocol.
Breaking Down Polkadot’s Network
As stated numerous times throughout Polkadot’s marketing and documentation, they rely on ‘Substrate’ to serve as the backbone of their actual network.
Therefore, any and all information about the network structure of Polkadot must be ascertained from Substrate’s documentation (as ‘substrate’ is mutually exclusive from Polkadot as a project).
This fact is enumerated directly on Parity’s website (creators of Substrate). Specifically, they state:

With that being said, if we chase down Substrate’s documentation on how they’re implemented, we find our answer on the library / structure they use to orient the actual network of Polkadot.
It is stated (verbatim) that:
“To ensure that nodes can join or leave the network at any time without affecting overall network connectivity, Substrate uses the Rust implementation of libp2p, a promising network stack that has everything needed to set up a decentralized network environment.”
Great! We just need to take a look at libp2p’s documentation and we should be up to speed on how nodes communicate on Polkadot’s network.
The design of networks using libp2p is outlined in explicit detail in their documentation.
See below:

Taking a Step Back to Look at the Bigger Picture
We’re getting a bit deep into the technicals here, so now is a good time to step back and remind ourselves what we’re doing down this rabbit hole:
A) Polkadot’s documentation details something called a ‘punishment fee’, which is doled out to “vaults” that do fail to prove it sent out the correct number of bitcoins to the correct address within a certain time limit

B) We challenged the implementation of such a standard by proposing it would be impossible to set a time limit on a vault since different peers on the network will find out about the vault requirement at different points in time (in fact, the entire network may have a different perception of the time limit). This cannot be reconciled by having one node get the time from the other because there’s no discernible way to tell if that node is lying or not. Additionally, there’s no way for that node to tell whether it is one of the first to have received the appropriate trigger to initiate the countdown
C) In order to prove our hypothesis true, we need to first establish how nodes are oriented on Polkadot’s network.
D) Since Polkadot uses Substrate (which we provided proof for), we began digging into Substrate’s documentation for more specifics on how nodes are oriented.
E) Substrate’s documentation indicated that they use the ‘libp2p’ library for node communication
F) Now we are on libp2p’s site and evaluating the documentation there to verify our assertion that Polkadot’s network communicates via ‘gossip protocol’, which means that one node tells a few nodes information it has received (relay), then those nodes tell a few nodes (each), and so forth until the information is propagated across the network

The picture above provides an accurate visual for how the gossip protocol works in this case.
Notice how each node is only communicating with 3 unique nodes, yet the total # of nodes receiving the information grows exponentially [O(n)<sup>2</sup>].
This is how propagation works on the Polkadot network. And while this is an efficient means of disseminating information on a p2p network, it introduces inevitable latency between messages (i.e., some amount of time must elapse between the receiving of a message and passing it on to a peer; this is a limitation of space, time and physics if we wish to preserve the property of ‘decentralization’)

As shown above (hopefully) the latency has a cumulative impact contingent on how many ‘hops’ must be made from the source to its destination.
Revisiting the Concept of ‘Locking’ Bitcoins on the Polkadot Platform
This may seem redundant, but it feels really worthwhile to take the time to go back and look at the notion of ‘cryptocurrency-backed assets’ (collateral) that Polkadot claims will be used to back its platform.
Within the ‘README’ of the interlay GitHub repo that we visited earlier, there’s a hyperlink to additional documentation on the protocol:

That link takes us here

Even though we’ve already reviewed this protocol (albeit, in a very topical manner) via the whitepaper we looked at earlier, it seems worth it to quickly go through this documentation here to see if there’s any greater clarification on the supposed ‘locking’ process that this protocol introduces to the interoperability equation that is liberal enough to be considered valid on the Bitcoin protocol but strict enough to restrict the sending user from arbitrarily accessing their bitcoins.
There is a diagram provided below, but it still doesn’t give us any greater information about what’s going on:

The design principles of this protocol are also flawed in a number of ways. But before we enumerate on those, let’s take a look at what they are below:

Great, so we have the promise of ‘secure audit logs’, ‘transaction inclusion proofs’, ‘proof-or-punishment’, and ‘over-collateralization’ (that last one is still a bit of a mystery since collateral should be wholly unnecessary if the process is trustless ; collateral is essentially an insurance policy on something that requires trust).
Flaw in ‘Secure Audit Logs’
According to the documentation, secure audit logs are logs that are, “Constructed to record actions of all users both on Bitcoin and Ethereum”.
This is a curious facet of the proposed protocol because there already exists such a construction. Its called ‘blockchain’ - literally, the distributed ledger itself where a record of all transactions are kept. Keeping another record is needlessly redundant, so this facet of the protocol design makes little to no sense.
Transaction Inclusion Proofs
According to the documentation:
“Chain relays are used to prove correct behavior on Bitcoin to the smart contract on Ethereum”
The first question that comes to mind is, ‘What exists to ensure that the chain relays are actually proving correct behavior?’ ; there seems to be nothing in the design that accounts for potential misbehavior by these relays. Therefore, we must trust that they’re going to do the right thing.
Objectively, there’s nothing wrong with this - but given the design goals of Polkadot, this undermines the project’s purpose.
Proof-or-Punishment
We already explored above why the ‘proof of punishment’, as specified will ultimately be ineffective (hint: Because there’s no way for the network to come to a consensus on how much time a vault has remaining because there is no way for the network to come to a consensus on when the trigger action began due to the gossip protocol).
Over-Collateralization
For this, the documentation states:
“Non-trusted intermediaries are bound by collateral, with mechanisms in place to mitigate exchange rate fluctuations”
There are a few confusing things here to be honest:
The first question that must be asked here is:
How is there even a question of ‘trusted’ vs. ‘non-trusted’?
According to the documentation on Polkadot’s website under “bridges” (right above the ‘Bitcoin bridge’ section):
“Bridge designs come in a variety of flavors ranging from centralized and trusted to more decentralized and trustless. Polkadot favors the latter bridge designs for its ecosystem…”
source: https://wiki.polkadot.network/docs/en/learn-bridges#bitcoin-bridge
Below is a screenshot of the documentation as well so that it can be read in its full context:

The documentation actually goes further than this, stating (on the same page) that:
“Bridges are specifically for making the Polkadot ecosystem compatible with external blockchains such as Bitcoin, Ethereum, or Tezos (among others). For information on XCMP, the native interoperability technology that allows parachains to trustlessly communicate, please see the dedicated crosschain page on the Wiki.”
While the XCMP is a bit different than what was described with the ‘XClaim’ protocol that is touted in other sections of the documentation, the same flaws still exist in the XCMP that existed in the XClaim protocol that we dissected earlier.
Wrap-Up
At this point, it feels like we’re beating a dead horse into the ground and its likely that most readers probably get the point by now.
Polkadot is a brilliantly designed project in many ways, with a ton of potential - but that potential is cut down short by its incessant need to take shortcuts on portions of the protocol that do not mandate such shortcuts be taken.
There are ways for Polkadot to integrate 1:1 transfers to their protocol in a manner that does not require them to use a ‘middleware’ protocol without a valid consensus, but that would require Polkadot itself to have a valid consensus algorithm (which must be Proof of Work, ultimately).
This idea and concept is one that the space will try vigorously to fight, but at the end of the day - its for the better of the protocol overall.
Auf komische und tragische Weise zugleich erzählt der Film die Geschichte von zwei Leuten mit unterschiedlichem sozialen Hintergrund. Auf der einen Seite der querschnittgelähmte, reiche Philippe, der in einem Stadtpalais mitten in Paris wohnt. Viele Mitarbeiter kümmern sich um Haus und Mensch. Auf der anderen Seite Driis aus der Pariser Vorstadt, dessen Mutter nicht seine richtige Mutter ist, mit vielen Geschwistern. Die Mutter geht putzen um die Famlie zu ernähren, die Kinder befinden sich am Rande der Kriminalität. Die Verbindung der beiden wird über den Pflegeberuf gesponnen, der ebenfalls sein Fett abbekommt. Driis erhält Arbeitslosengeld, muss sich dafür jedoch vorstellen gehen - und tut das bei Philippe. Wider Erwarten stellt er ihn zur Probe und später fest ein. Ein ständiges Spiel von Situationen, wo die beteiligten Personen nicht oder nicht genug über ihren eigenen Tellerrand hinaussehen, gibt dem Film einen roten Faden, wo man nie weiss ob man lachen oder weinen soll.
Basiert ist der Film auf dem Buch Le Second Souffle, einer wahren Geschicte von und über Philippe Pozzo di Borgo. Der Adelige, Geschäftsführer eines Champagnerhauses, ist seit 1993 querschnittgelähmt. 2003 wurde die Dokumentation à la vie, à la mort gedreht. 2017 wurde ein amerikanisches Remake von “ziemlich beste Freunde” gedreht, the upside, das jedoch nicht an das Original herankam. Philippe Pozzo di Borgo verkaufte 2010 sein Stadtpalais hôtel Pozzo di Borgo für 100 Mio Euro an die Regierung von Gabon, Ali Bongo, und lebt heute in Essaouira, Marokko. Der Algerier Abdel Yasmin Sellou, der Pozzo die Borgo 10 Jahre betreute, betreibt heute einen Hühnermastbetrieb in Algerien.
Life is Strange (reviews) established the team at Dontnod Entertainment as talented storytellers and worldbuilders. The game was a joy to explore and offered meaningful player choices that elevated it above the status of mere “walking simulator”. The story it told had a definitive ending; what, then, could a sequel have to offer?
While Life is Strange 2 occupies the same universe and is structured in a similar episodic format, it tells a completely new story, setting the series up as an anthology—think Fargo or True Detective, not Stranger Things.
The second season is about a 16-year-old kid named Sean Diaz and his little brother Daniel. After a traumatic incident, Sean and Daniel find themselves running away from home and wanted by the police.
As the player, you control Sean’s actions and define the kind of relationship you will have with your brother, and with the world you both inhabit. Will you and Daniel steal food to survive, or beg for scraps? Will you attack those who wrong you, or forgive them? Will you trust in the kindness of family and strangers, or face the odds on your own?
The story takes place in America under Donald Trump, but the writers make a point to include moments of love and tenderness alongside the darkness of racism and prejudice that Trump represents.

A story told by Sean to his little brother sums up the events so far at the beginning of each episode. In the story, Sean and Daniel are “wolf brothers”. (Credit: Dontnod Entertainment. Fair use.)
Warning: The text below contains spoilers.
Like the first season, Life is Strange 2 has a supernatural element. Early in the game, it becomes clear that Daniel possesses significant telekinetic powers. As the player, you coach Daniel on when and whether to use his powers, but you do not control them directly, and your choices are not reversible.
Life is Strange 2 improves on the first game’s graphics, which is especially noticeable during the sequences where you explore natural environments like the forests of Washington and Oregon, or a canyon in Arizona. Like the first season, the game is fully voice-acted. Unfortunately, I felt that Gonzalo Martin (Sean Diaz) often overacted his part, which is significant because he’s the main voice you’ll be hearing throughout the game.
Besides making choices and occasionally solving small inventory-based puzzles, you also get to collect souvenirs on the road, which you can inspect in your backpack later. Moreover, Sean Diaz is an aspiring artist, and at various moments you can sit down and draw in your sketchbook. You don’t directly control the pen, but you can choose between different ways Sean sees the world: Is a room you’re trapped in a prison, or can you already see a stairway to freedom?

In the last episode, you and Daniel briefly explore a canyon in Arizona, showcasing the game’s significantly improved graphics. (Credit: Dontnod Entertainment. Fair use.)
The first Life is Strange ultimately presented the player with a choice between two very different endings. Life is Strange 2 builds towards a similar choice, but the endings depend not just on that one decision, but on the cumulative effect of your actions so far. For my playthrough, this worked really well. I felt that the ending corresponded beautifully to how I had chosen to act as Sean. That’s a rare feat for a game.
I enjoyed the game, and recommend it. Like the first title, it depends heavily on the chemistry between two characters—in this case, Sean and Daniel. I did not find those characters quite as compelling as Max and Chloe in the first game, partially due to the voice acting, and partially because playing out an at times strained relationship between two siblings is just more emotionally exhausting.
I would rate the game 4.5 stars, rounded up because the team at Dontnod clearly poured their hearts and souls into this game. If you’re looking for mindless escapism completely detached from reality, this is not the game to pick, but if you invest yourself in its story and characters, the game rewards you with a narrative arc that truly feels like you’ve made it your own.
